aNewDomain — Cyber jihad, in which organizations attack, humiliate and threaten entities through the Internet, should be seen as part of the developing tactic by ISIS, North Korea and other factions. Cyber warfare is not just about getting secrets, it’s about embarrassing your enemy, as we all saw in The Interview Sony debacle.
ISIS is already here, in your PC and in each military base. It doesn’t have to storm the walls, it just has to hack effectively. The most recent example of this is the official messages released by Centcom that its Twitter account was hacked by backers of ISIS. The hackers said the feat was done with “Allah’s permission.”
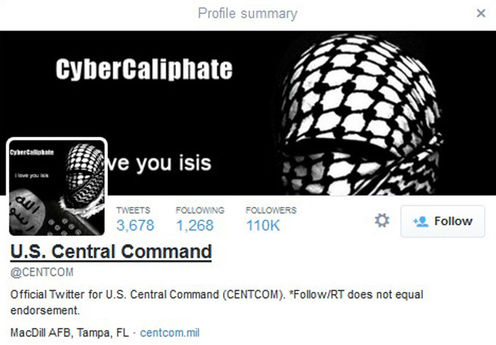
Image Credit: Screenshot by Reuters
Cyber Jihad on Centcom
On Jan. 12th, in the afternoon, the US Centcom’s Twitter and YouTube accounts were shut down. ISIS affiliated hackers made a public showing of their social media arm just to get more headlines. As criminals and terrorists become more adept, defense agencies worldwide are playing a continuous cat and mouse game. Often there are attacks against national services, but these go unreported when the offenses are successfully deflected.
But, as we all saw, that didn’t happen this time.
The Central Command Twitter site was filled with threats that said things like, “American soldiers, we are coming, watch your back.” Other postings appeared to list names, phone numbers and personal email addresses of military personnel as well as PowerPoint slides and maps. Most of the material was labeled “FOUO,” which means “For Official Use Only,” but none of it appeared to be classified or sensitive information, suggesting the hackers did not breach classified material.

Image Credit: Screenshot by Reuters
Twitter Account Security
Twitter’s Basic Account Settings allow you to control how people can find your profile, what information you share and the level of security your account requires when you are using the web-browser based version of Twitter (that is to say, not a client, smartphone app or GSM phone). You can find more on security settings here.
In the settings of Twitter there’s a “Tweet Privacy” section. Here, Twitter allows you to control who can see your tweets: the public in general, or only individuals who you allow to follow you.
Is Centcom not aware that even if you choose the “Protect My Tweets” option, the Tweets are still accessible to Twitter and therefore can still be recorded and handed over to third parties?
You (yes, you) are probably not a target of North Korea or ISIS, but there are hackers and trolls who might like to disrupt and take revenge on you personally some day, in some way. So be aware, and wiser to the cyber dangers than Centcom was.
Centcom issued a statement that no operational damage was done, and that Twitter was hacked, not Centcom itself …
But — hello military dudes! That was not the point. It’s all a propaganda and media war in cyber space. The timing of the hack was perfect, and the embarrassment that followed will certainly happen again.
For aNewDomain, I’m David Michaelis.