aNewDomain — Just after 9 p.m. ET on Sunday, July 19, Brian Krebs found a new message in his Gmail, sent by someone from the address ImpactTeam@Ashley.Madison.com. Its subject line: Ashley Madison Was Hacked.
— Just after 9 p.m. ET on Sunday, July 19, Brian Krebs found a new message in his Gmail, sent by someone from the address ImpactTeam@Ashley.Madison.com. Its subject line: Ashley Madison Was Hacked.
Now, a lot of people would’ve sent such an email directly to spam. Not Krebs. An independent journalist and security expert, Krebs has built up a real reputation for covering and analyzing some of the world’s most high-profile retail hacks. So Krebs opened it, he told me, and this is what he found inside:
This mail is sent via contact form on Krebs on Security http://krebsonsecurity.com – DO NOT HIT REPLY
News tip: Ashley Madison, the world’s #1 affair/cheating online dating site, has been hacked.
http://imgur.com/8gQs8KV
https://bitbucket.org/TheImpactTeam/ashley
https://bitbucket.org/TheImpactTeam/ashleymadisondump
https://gitlab.com/ImpactTeam/ashley
https://gitlab.com/ImpactTeam/ashleymadisondump
https://launchpad.net/ashley
https://mega.nz/#!f4smmDCa!YM7eJE2uxDvjGhxPERYk5tgBgeRyZoEYc9d0JMFUCP0– – – – –
This mail is sent via contact form on Krebs on Security http://krebsonsecurity.com – DO NOT HIT REPLY “
It seems like a lifetime ago, I know, but in mid July, when Krebs first opened that email, the Ashley Madison name and signature image weren’t universally recognized the way they are now, after two months of sensational non-stop coverage by seemingly any outlet that can say “news,” much less print it.
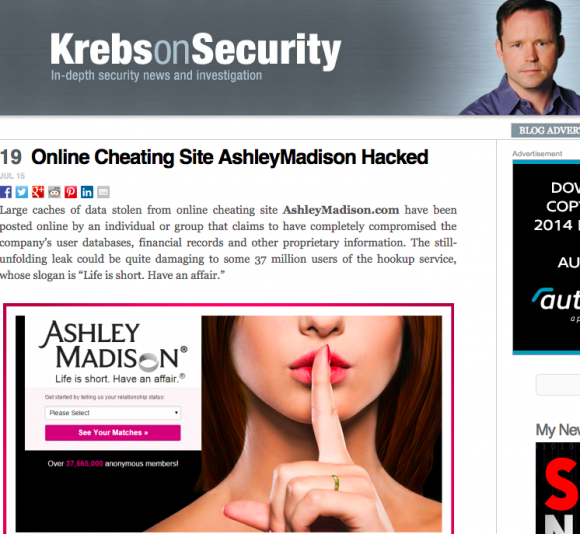 The media circus around the Ashley Madison hack scandal is among the most intense in recent memory. And, that it centers around a fairly small Canadian tech company, even one that’s earned some notoriety for a website billed as an “extra marital dating site” that links men to married women, is stranger still.
The media circus around the Ashley Madison hack scandal is among the most intense in recent memory. And, that it centers around a fairly small Canadian tech company, even one that’s earned some notoriety for a website billed as an “extra marital dating site” that links men to married women, is stranger still.
The links in the email, as you can tell, no longer work and they only worked for about 50 minutes after he recieved the message, Krebs told me.
When he initially tried them, they led to many of the images and statements you’ve by now seen hundreds of times since the scandal began: images including the colorful “Impact Team” hacker ultimatum, demanding that Avid either shutter Ashley Madison and a so-called “sugardaddy” hookup site “EstablishedMen.com” or see the worldwide, embarrassing release of all the names, numbers, financial details and sexual details of its some “38 million members.”
Closing the sites, the statement read, would cost, but it wouldn’t cost as much as what would result if the hack were released.
What convinced Krebs there was something to all this were the links pointing to a sampling of sensitive-looking internal documents belonging to Avid.
 Krebs confirmed, first, that this was a story not yet widely reported. It wasn’t anywhere. Next, he found a posted company phone list containing direct extensions for Avid execs, including its CEO Noel Biderman.
Krebs confirmed, first, that this was a story not yet widely reported. It wasn’t anywhere. Next, he found a posted company phone list containing direct extensions for Avid execs, including its CEO Noel Biderman.
At around 9:20 p.m that Sunday night, he dialed Biderman (left), who picked up. Biderman confirmed the breach by telling Krebs he “couldn’t deny” it, Krebs says. Biderman also told Krebs he was pretty sure he knew the culprit — likely an insider whose face was on a screen Biderman said he was looking at right then.
As for the email and links and sampling of apparently internal company docs? The real thing, Biderman said. After the two finished their half-hour discussion, Krebs set about writing up his scoop.
Krebs posted the story — read it here — by 11 p.m. ET on his security-focused blog. By then, the links no longer worked, which made sense, thought Krebs, if Biderman really was so sure of the person who breached the Avid network. A few thousand people might’ve seen the story by the time he went to sleep that night, Krebs said, which is why he was stunned the next morning to learn that news of the hack was everywhere.
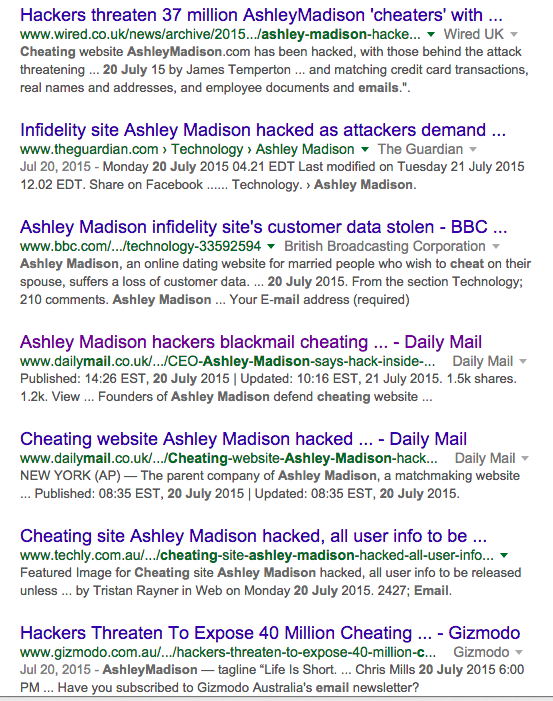 The stories, most of which carried the dateline “MailOnline” quoted Krebs’ story and the short Biderman interview, but they also claimed that “millions” of Brits were panicking that hackers might publicly humiliate them for joining the site. The stories included interviews with the actual hackers –“one, named as (sic) Pernell,” the piece said — and an interview with one of the female “victims.”
The stories, most of which carried the dateline “MailOnline” quoted Krebs’ story and the short Biderman interview, but they also claimed that “millions” of Brits were panicking that hackers might publicly humiliate them for joining the site. The stories included interviews with the actual hackers –“one, named as (sic) Pernell,” the piece said — and an interview with one of the female “victims.”
Even stranger, that first story also included the screens he’d found in that anonymously sent email’s links — links that were only live for less than an hour after he viewed them and took screenshots. Countless media reports after showed the same screens. Krebs began wondering how all the international news organizations had gotten them.
How was it that a whole continent had heard of his story just a few hours after it ran and even managed to find hackers and victims to talk to on the record.
All the pieces, looking back, had one thing in common.
The stories all seemed like copies or versions of the first one, which carried the dateline of MailOnline.
A media circus was immediately born, with hundreds of news stories showing up daily, captivating readers all over the world with wildly colorful, fabulous tales and lots of unlikely sounding details around panicking Ashley Madison members in Britain who feared “the Impact Team,” according to MailOnline. Soon, countless other news outlets, small and large aroung the world, were carrying the same story.
***
That someone breached Avid sometime in mid July or a bit earlier seems pretty hard to debate. I’ve examined and verifed a good chunk of the some 175K-plus internal Avid emails that were dumped online on Aug. 21 and 22. They’re still available on Internet sites like this one, which Twitter user and self-described “piracy advocate” @amlolzz maintains and promotes to a busy stream of journalists looking for more Avid/Ashley Madison news.
Then there are the customer lists, source code and other personal data that the same culprit(s) are now alleged to have released days earlier, reportedly after Avid didn’t shutter its Ashley Madison and EstablishedMen sites as ordered.
I haven’t seen, searched for or verified these lists, but several reporters and individuals who found their own information on the lists say they’re the real thing.
Of course, as you’d expect from a site that doesn’t verify emails, some of the names appear to be way off. Few maintain, for instance, that Tony Blair joined Ashley Madison using his official and publicly-known work email.
Also, there’s the issue, as originally discussed by Gizmodo, that the overwhelming majority of the some 30M email names belonged to men. And many of the few female accounts, it’s said, belonged to “engager” bots.
That’s a common practice among adult dating sites, according to hundreds of user reviews of Ashley Madison and competitor sites. This story, from a blog called the CleverCourtesan, made the Internet rounds a couple of years ago, and even claimed it knew what software Avid was building.
So, yes, the “hack” or “leak” or “breach,” however you want to couch it, doesn’t at all appear to be made up.
But so many of the other details around the Ashley Madison story as it exploded on July 20 are, on examination, either questionable or just plain wrong. This investigative piece employs internal docs, online evidence, interviews with former Ashley Madison execs and consultants and other data to take a look at these details — by now mostly accepted as facts.
How did it happen? Well, let’s look at the first pieces that appeared in hundreds of news media outlets across Europe, Asia, the UK and finally the U.S. (Note: The first MailOnline article I found days ago, that appeared in an India outlet with a timestamp of 10 a.m., is no longer loading. I’m replacing it with the identical looking MailOnline piece that appeared in another outlet, though much later in the day on July 20, below …)
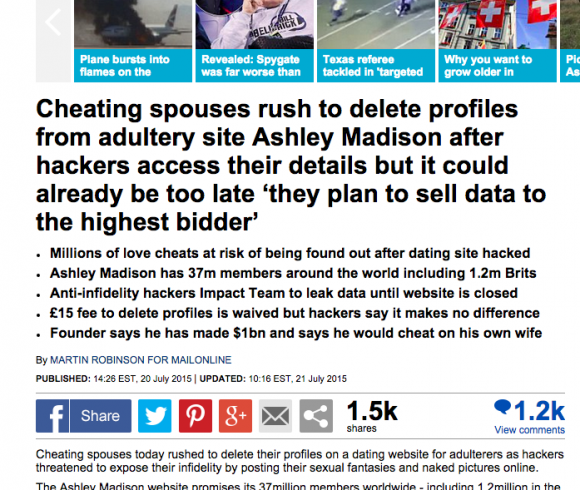
So who is MailOnline and how did a single story it ran, entertaining and fantastic as it was, end up cloned or heavily excerpted in practically every corner of the world so quickly?
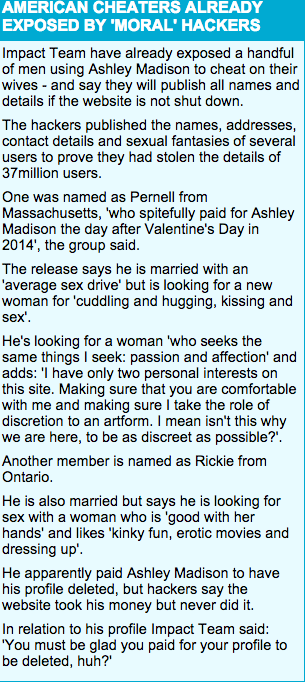 That’s a straightforward question. MailOnline, according to data published in the Financial Times and quotes from its own founder, isn’t always a straight news service, which you’d probably guess if you just took a couple of seconds to look at that first Ashley Madison piece in that publication. One of that first story’s colorful sidebars is readable at lefe.
That’s a straightforward question. MailOnline, according to data published in the Financial Times and quotes from its own founder, isn’t always a straight news service, which you’d probably guess if you just took a couple of seconds to look at that first Ashley Madison piece in that publication. One of that first story’s colorful sidebars is readable at lefe.
Rather, it’s one of the biggest players in the field of paid sponsored content or the harder to identify “native advertising” a type of sponsored, or paid, editorial content that’s breezy and entertaining to read, professionally designed to look like the real articles around it, and engaging enough to be widely shared and consumed.
The Financial Times describes the phenomenon of sponsored content and native advertising, as it appears in services around the world. It describes such stories as “the most contentious variety (of sponsored content)” designed to “look the same as the editorial content of a particular website … and blend in seemlessly” with its other stories.
The cost? About 65K per “campaign” a month, a price that included a guarantee of no fewer than 400K views, the FT and others have reported. This appears to be accomplished, when you examine it, by a wire-service-like method of online distribution.
For instance the Ashley Madison piece that ran MailOnline, sensational or not, immediately showed up on a small town online news site in India, several others in South Africa, Nigeria, Malay, Taiwan, Hong Kong and countless second and third tier news markets around the world. Then again, we found other paid media outlets who also were passing the story around that morning. (updating)
We have no evidence pointing to who, if anyone, would’ve paid for an Ashley Madison campaign around the hack, whether it’s called native advertising, sponsored content or anything else.
MailOnline editors, when contacted yesterday, wouldn’t comment on this story.
UPDATE September 11, 2015:
A report in Fusion today quoted an unnamed spokesman at MailOnline as saying that Ashley Madison hack coverage …
… was not paid-for content and the entire premise of the story is false … native advertising on MailOnline is clearly marked as such, and we reject in the strongest terms the claim that the article which the piece focuses on, which appeared well after the news of the Ashley Madison hack emerged, was fabricated. We have written to the website formally to request that the incorrect allegations are removed without delay.”
We here at aNewDomain eagerly await the opportunity for on the record clarifications from MailOnline and to learn the name and contact deals for the “spokesman” Fusion quoted as saying the above. A rep has yet to contact this writer.
Update Sept. 13, 2015
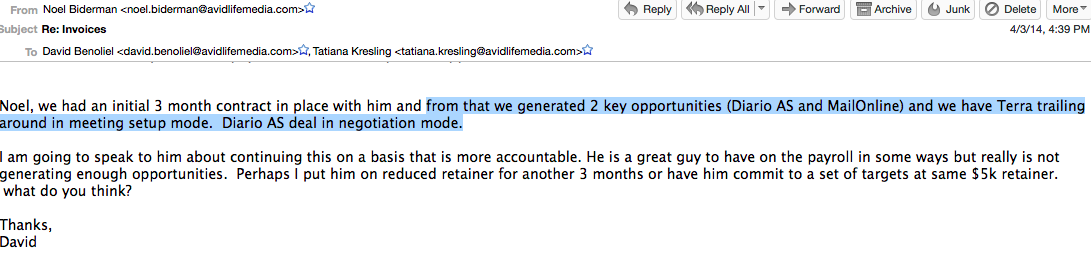
We have yet to find an invoice or anything else in the leaked emails showing that Avid or AshleyMadison as a site had a deal with MailOnline to create sponsored stories (labeled) or native advertising pieces (unlabeled) but in one April 2014 email, execs discussing a consultant’s future with the company, do say that he’d brought the company deals from MailOnline and Diario AS. Invoices for the Diario AS deal, which was for promoted content and promotion in Latin America, are in the cache of leaked emails allegedly sent by Biderman. What the MailOnline deal and invoices looked like, if it was struck, as the following email implies, have so far not surfaced in our analysis. Here’s what the DiarioAS pitch looked like, according to the leaked emails.
What’s weird about those first MailOnline stories?
If you read the excerpt from that first article, above left, you can see it doesn’t read like anything else I’ve found in that day’s stories — there are broken English constructions like “another member is named as Rickie” and “one was named as Pernell.” It also mentioned more than a million UK former Ashley Madison panicking about the hack, though news of the threat was barely out. And it had interviews with them.
Like so many firms, Avid is no stranger to this promoted content and native advertising deals. Here’s a contract we verified that details how Avid shell Pernimus worked with another major native advertising firm to the tune of some $100,000 a month.
Here’s a pitch from another native marketing company, Diario AS, to Ashley Madison. It went to contract, our email analysis suggests and one source close to the company verified for us …
MailOnline, it’s worth noting, should be no stranger to any major media outlet who found its Ashley Madison story interesting and worth re-running or excerpting, as NPR, CNN, Time and many others did that day. That’s because the service has always been controversial, to wit:
- A 2009 MailOnline piece about a “solar panel made of human hair,” which Geek.com reported as a hoax.
- A January 2012 article widely circulated around the world claiming that Advertising Age selected a Rihanna ad for “sexiest ad of the year” was untrue, leading The Huffington Post to remove the piece, saying it “seemed to originate from DailyMail.”
- An April 2012 MailOnline story, bylined by reporter Simon Tomlinson, relating the tale of a dentist who extracted her former boyfriend’s teeth was “a hoax,” according to an MSNBC expose, which also noted Tomlinson’s remark that he “did not know where the story came from.”
- An October 2012 story in MailOnline that alleged actor Nick Cage was guilty of tax evasion, a story for which Cage won damages and a MailOnline apology.
- A July 2014 MailOnline post about actor George Clooney and his then-fiancee’s family circumstances, which MailOnline leadership did admit as being “entirely false.”
Also: Most if not all of the Ashley Madison coverage that followed Krebs’ piece and the native advertising piece that ran in MailOnline accepted as fact that the attack resulted, in part, by hackers angry over the way Ashley Madison execs dealt with customer data. Various quotes tracing back to those first stories claim that Avid’s PayDelete offer was bogus. The $15 fee was supposed to ensure the company wiped identifying data off servers. But in those stories, the “Impact Team” statements as quoted said they didn’t.
Internal emails that have come to light seem to contradict that, though.
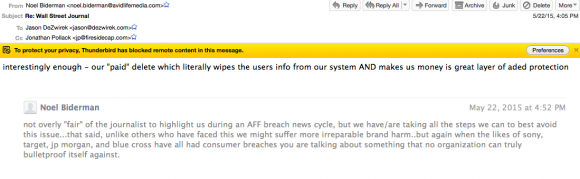
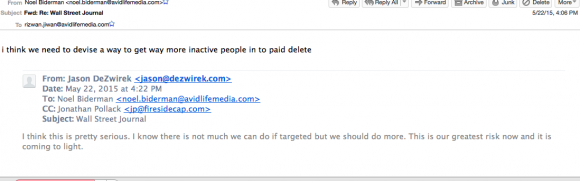
Take a look, below. There are three internal emails that seem to support Biderman’s original assertion to the media early on that the $15 paid delete function was genuine and, actually, worked. That matches one of the very earliest stories, from the Washington Post, that quoted Biderman denying the hackers’ claim.
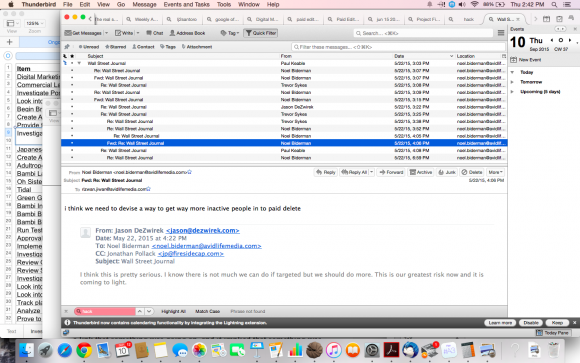
See the email exchange below, dated May 22, 2015. It’s between Biderman, board member Jason Dezwirek and other execs the day AM competitor Adult Friend Finder was hacked.
If only the firm could get more users to pay for the “pay delete” feature, Biderman mused, the firm’s data would be decidedly more secured …
Also, the first media reports incorrectly characterize Ashley Madison as just a dating business and Avid as just a dating business network. Here’s how it really makes its money …
![]() Another Ashley Madison hack myth as promulgated by the first native advertising pieces and the mainstream news reports that followed is the portrayal of Ashley Madison as just a dating site or that Avid just runs a dating site or “social network,” as the Toronto Police characterized the firm in a press conference last week.
Another Ashley Madison hack myth as promulgated by the first native advertising pieces and the mainstream news reports that followed is the portrayal of Ashley Madison as just a dating site or that Avid just runs a dating site or “social network,” as the Toronto Police characterized the firm in a press conference last week.
 Last week, OkCupid CEO Christian Rudder told Inc. magazine earlier this week that Avid/Ashley Madison “wasn’t a dating company” but, rather, a “scam.”
Last week, OkCupid CEO Christian Rudder told Inc. magazine earlier this week that Avid/Ashley Madison “wasn’t a dating company” but, rather, a “scam.”
I found no evidence or allegations suggesting there was a scam going on, but otherwise, Rudder seems to be dead on. Avid’s business isn’t dating, it’s in the running of an enormous, international direct marketing affiliate network with 1000-plus partners generating killer cash profits every single week. Here’s a quick snapshot of one week in June 2015, a summary of weekly revenues coming in for the long list of affiliates, grouped by sales managers.
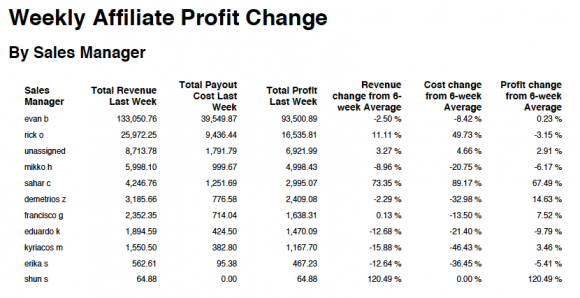
Using corporate docs I independently verified and date from that sample week in June, I developed a clear financial picture of just what that furious rev engine looks like.
One Avid affiliate, an escort service type listing site called Escorts.CA, generated more than 13K in revenue in just that week, 60 percent of which Avid enjoyed as pure cash profit, I verified through former Ashley Madison consultants close to the affiliate biz and through leaked docs now widely available over the Internet.”
What’s Escorts.CA? According to this piece in the DailyDot, it’s an escort service site originally created by an Avid exec, John Santora, whose name appears in the spreadsheet row (below) as the “affiliate” username.
Here’s a leaked Google Doc that shows the pitch and early deal terms, as negotiated.

Now check out the data around a very different affiliate partner, one most tech readers of this publication will know well. It’s one time tech media giant Ziff Davis, an enterprise for who I once worked as a beat reporter covering operating systems throughout most of the 1990s.
“The truly valuable partners for (Avid),” the former consultant I spoke with on condition of his anonymity explained, “aren’t the porn industry ones. It’s the ones who reach (the valuable) the demographic of well-heeled, tech savvy early adopters of gadgets and online consumer services.”
As you can see below, for the sample June 2015 week I looked at, Ziff performed really well. It was able to generate a healthy stream of click-throughs to Avid properties via a male gadget lover themed magazine. Ziff Davis brokered an Avid affiliate deal for the themed magazine, I verified through docs and interviews with individuals close to that partnership.
Those clicks, according to the spreadsheet row below, generated $1,895.30, got paid $1,000 and generated $895.30 for Avid, in just that week. That number is about the average of what the affiliates bring in to Avid weekly, sources close to Avid verified to me. Internal documents circulating around the net show in weekly reports going back three years or more the same thing.
![]()
To get an idea of the size and importance of this revenue network for Avid, consider that Avid appears to have generated a total of $144,91.28 (rounded) FOR ONE WEEK, a number that’s fairly middling for Avid considering reports I compared year to year. And 60 percent of that fat little amount was pure cash profit to the mothership.
“Avid” can be taken to mean Avid Dating Life (ADL), dba Avid Life Media, Cougar Life Inc., Established Men Inc., Pernimus Ltd., ADL Europe and many more Canadian, Delaware, Cyprus and British Virgin Island entities listed here.
And there are so many other sites in the portfolio besides just AshleyMadison.com. Have you seen its big sis, the hard core Ashley Madison porn listing site AshleyRNadison? And then take a look at CougarLife, Date Mrs.Robinson, EstablishedMen, ManCrunch, The Big & The Beautiful and white label partner sites like ArrangementFinders.com, ErosDating.com and DateBrokeCollegeGirls.com and so many more that we’ve found …
All of these, remember, aren’t dating sites designed to build communities and loyal members (like, say, a Match.com). Rather, they’re promotional vehicles proven to grab a ton of press attention and controversy in any market where they first open up.
Why didn’t “hackers” ever attempt to show this intricate business model, or the lists of 1000 affiliates presumably with identities and negotiated deal s they’d rather stayed quiet? Why not write about all those sites, not to mention multiple paid promotional media deals with such sites as The Huffington Post, which one sales associate, in a happy email to Biderman, we’ve confirmed, announced would commit to regular Avid-created news pieces in its dating section. HuffPo as yet has not responded to emails for comment.
s they’d rather stayed quiet? Why not write about all those sites, not to mention multiple paid promotional media deals with such sites as The Huffington Post, which one sales associate, in a happy email to Biderman, we’ve confirmed, announced would commit to regular Avid-created news pieces in its dating section. HuffPo as yet has not responded to emails for comment.
Assuming that “hackers” really did set out to take down Avid, why didn’t they focus on the real business or threaten to out all those respectable tech media partners, like Ziff, or threaten to announce to all those foreign press outlets eager to drink in spicy marital dating site numbers? Why didn’t the hackers say that really it was all just paid-for promotion, or however poorly it could characterize it?
Did the “hackers” really not kno w? Even though thousands of emails in their own, supposedly hacked Avid corporate email dumps discuss all this openly and constantly? Did they not care?
w? Even though thousands of emails in their own, supposedly hacked Avid corporate email dumps discuss all this openly and constantly? Did they not care?
If the hackers really wanted to get dirty, they could’ve began to publicize the secret plans afoot at Avid to build out a full data analysis and anonymized data aggregate business, like what Google and Facebook are built around, one Avid former exec told me.
Were some of the “cybersecurity” experts who validated the hack and warned of “dark web blackmailings” bogus? Well …
Just when you thought the most outrageous Ashley Madison fictions and developments were behind you, you run into something so crazy you think someone must be pranking you.
As I was trying to verify the background of a “high-ranking cybersecurity official” who appears in so many of the paid content stories verifying the hack and anticipating other somewhat shocking and definitely dramatic developments, like Ashley Madison suicides and dark web blackmailings, I ran into something bizarre.
Meet Stuart Hyde.
He’s the so-called “Europol” cybersecurity expert who keeps popping up in the Ashley Madison hack coverage. Here’s a HuffPo UK piece that featured him.
Here’s his LinkedIn profile (left)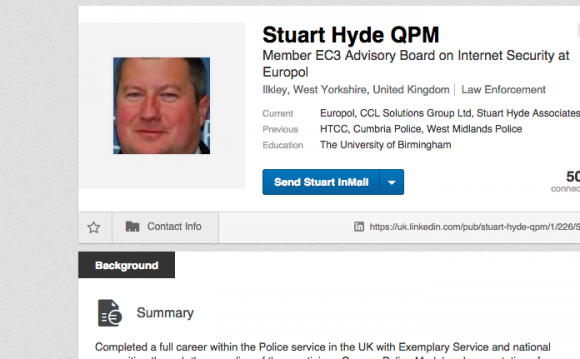 .
.
Notice he claims he is a “Europol member and advisor on its EC3 digital crimes unit … retired Midlands police offer awarded with a Queens Police Medal (sic) for exemplary service” and has received an “Honorary Doctorate for commitment to Cybercrime prevention and detection.”
I’ve reached out to Europol to confirm the first two claims. Its public information officer emailed me today and told me it could be a day or two before they confirm one way or the other …
Hyde, who runs Stuart Hyde Associates (SHA), a consultancy that focuses on “digital risk … (and) digital forensics” actually seems to be a retired or former officer from Umbria, I determined.
This contradicts several stories I easily found online, stories that claim Hyde in reality was a former Midlands cop, as well as the “shamed and discredited” Umbria constable who was the focus of a misconduct investigation.
Then, oh no! I started finding report after report saying Hyde is the same “former cop” who this report says fell into a COMA in mid April 2015 after a glamourous-sounding business trip to the Middle East on “official IT business.”
And just as I was starting to feel guilty, I found another series of reports talking about that coma and April 2015 hospital stay, only these said the patient here wasn’t named “Hyde” but a conman with “many aliases” named Michael Knight of Swansea, Wales.
According to this report, in August he faced 18 counts of theft and fraud for “swindling a frail 86-year-old man with dementia out of more than £41,000.” 
A follow up story alleges, in large headlines, that “Wright” (shown below in an arrest photo) FAKED the coma in April and falsely claimed to police afterward that he was paralyzed from the neck down (!) and so was “too ill to stand trial” for the fraud charges … I have a call out to the person who tweets as Stuart Hyde …
Two other security officials I found in the paid content stories also didn’t check out, as you’ll see in the final part of this report …
… DEVELOPING … THIS STORY IS STILL LIVE ...
For aNewDomain, I’m Gina Smith.
Here’s the Globe and Mail rate card for paid content.
Ashley Madison/Native Advertising: Globe Digital Mediakit 2015 (1)
 FURTHER READING/LINKS:
FURTHER READING/LINKS:
Ashley Madison Investigation: Who Is Brian Offenheim
Bondage, Escort Listings, Live Video, Porn Sites Fill Ashley Madison Lineup
Leaked Ashton Madison Emails: Avid Tried To Trick Nightline with Fake Members, Fake Stats
AshleyMadison Isn’t A Dating Site, But A Huge International Direct Marketing Affiliate Biz
Here is a doc someone loaded to Scribd months ago on Avid letterhead, which lists the various Avid operating company shells registered in Canada, Delaware, the British Virgin Islands and Cyprus.
Avid Life Media Legal Entities by Gina Smith
Here’s a contract I verified as authentic from the leaked Ashley Madison files. It’s a contract between Avid shell Pernimus and one of the biggest paid content (native advertisement) placement and promotion services online.
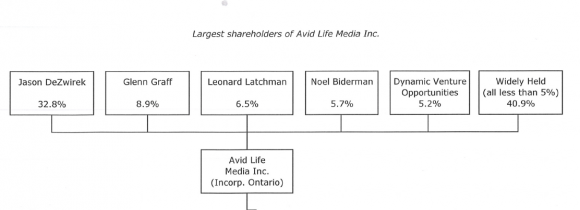
From the leaked email, as shared with me late last week, here’s a chart detailing ownership in Avid as of 2013.
AVID (dba Pernimus) Paid Content Contract (verified)
Ashley Madision: Not A Dating Business, But A Huge Direct Marketing Network …
Who Is AshleyRNadison.com? Ashley Madison Affiliate/White Label Sites Drive Affiliate Signups …