Update Dec. 29. 2016: U.S. President Barack Obama has announced sanctions against “four Russian individuals and five Russian entities” for “election interference.” The U.S. also will close two Russian compounds and 35 Russian diplomats to leave the country, according to this official White House statement. Find Obama’s Executive Order here.
aNewDomain — Confirming that Russia set out to influence the course of US elections, law enforcement officials today released the joint DHS-FBI report on Russian hacking, an effort they dubbed “Grizzly Steppe.”
The report arrived a day after Pres. Barack Obama announced the nation will sanction against all Russian individuals and entities who were involved in election-related hacking efforts by Russian intelligence.
In its statement, dated Dec. 29, 2016, the Department of Homeland Security, the Office of the Director of National Intelligence and the FBI said their joint investigation determined the hacking was “part of a decade-long campaign of cyber-enabled operations” directed at the American people.
The 13-page report is now declassified and readable in full below the fold. Ed.
As you’ll read below, the report details “the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. government, political, and private sector entities.”
The report appears to confirm at least some of what outgoing Senate Minority Leader Harry Reid claimed to FBI Dir. James Comey in an angry October 30, 2016 letter. Blasting Comey for falsely implying the agency was reopening its investigation into Democratic presidential candidate Hillary Clinton’s improper email server, Reid said Comey was guilty of a “disturbing double standard.” On one hand, said Reid, Comey refused to publicize what he called “explosive new evidence” tying Donald Trump’s campaign to Russian intelligence hacking efforts. At the same time, he “jumped at the first opportunity” to use innuendo to cast Clinton in “the most negative light possible.”
The report makes no mention of Russian ties to the Trump campaign, however. “This activity by RIS is part of an ongoing campaign of cyber-enabled operations directed at the U.S. government and its citizens,” the report says.
“These cyber operations have included spear=phishing campaigns targeting government organizations, critical infrastructure entities, think tanks, universities, political organizations, and corporations leading to the theft of information,” it continues. “In foreign countries, RIS actors conducted damaging and/or disruptive cyber-attacks, including attacks on critical infrastructure networks.”
It continues:
“The U.S. Government confirms that two different RIS actors participated in the intrusion into a U.S. political party. The first actor group, known as Advanced Persistent Threat (APT) 29, entered into the party’s systems in summer 2015, while the second, known as APT28, entered in spring 2016.”
This story continues below the DHS-FBI report that is readable in full below.
Grizzly Steppe: DHS FBI Report on Russian Hacking by Gina Smith on Scribd
The report is divided into several distinct parts. The first two summarize the findings of DHS and FBI investigators. It then moves into technical details explaining how they determined that Russian hackers were in fact behind the election-hacking and strategies US and corporate IT professionals should use to secure their networks to DHS standards.
Who hacked into US computers — and why?
According to the report, “the U.S. Government confirms that two different Russian intelligence (RIS) actors participated in the intrusion into a U.S. political party. The first actor group, known as Advanced Persistent Threat (APT) 29, entered into the party’s systems in summer 2015, while the second, known as APT28, entered in spring 2016.
Check out the DHS-FBI illustration below. The report says it portrays just how APT29 and APT 28 attacked the systems they targeted.
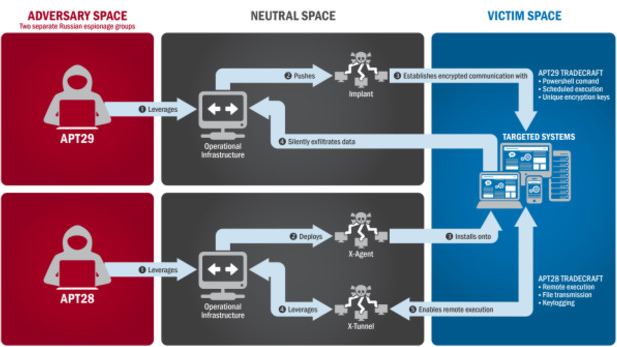
The report claims that both hacking groups, APR29 and APT 28, attacked not just government organizations (including, it says, “a US political party”) but also computer systems and networks at American universities, think tanks and corporations.
About APT29 hacking activities, the report claims:
“APT29 has been observed crafting targeted spear-phishing campaigns leveraging web links to a malicious dropper; once executed, the code delivers Remote Access Tools (RATs) and evades detection using a range of techniques.”
APT28 — a hacking group US officials said “is known for leveraging domains that closely mimic those of targeted organizations” — was all about tricking network users into entering their network ids and passwords. “APT28 actors relied heavily on shortened URLs in their spearphishing email campaigns,” according to the report, which continues with this:
“Once APT28 and APT29 have access to victims, both groups exfiltrate and analyze information to gain intelligence value. These groups use this information to craft highly targeted spearphishing campaigns. These actors set up operational infrastructure to obfuscate their source infrastructure, host domains and malware for targeting organizations, establish command and control nodes, and harvest credentials and other valuable information from their targets.”
Summer 2015: Russian hackers got into “a US political party,” says report
During the summer of 2015, according to the report, Russian intelligence-backed hackers in the so-called APT29 group mounted a fierce spear-phishing campaign via email.
The emails, which US investigators claimed targeted more than 1,000 individuals in US government and elsewhere, contained malicious links that turned US and educational computer systems into malware and spear-phishing hosts.
“In the course of that campaign, APT29 successfully compromised a U.S. political party.”
“At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware, said the report, adding that” APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.”
And in Spring 2016, FBI investigators say, Russian hackers attacked again
In spring 2016, APT28 again compromised the same political party, according to the report.
“This time, the spearphishing email tricked recipients into changing their passwords through a fake webmail domain hosted on APT28 operational infrastructure,” the report claims. “Using the harvested credentials, APT28 was able to gain access and steal content, likely leading to the exfiltration of information from multiple senior party members.”
That’s the data, says the report, that was leaked to the press and disclosed to the public, presumably via Wikileaks.
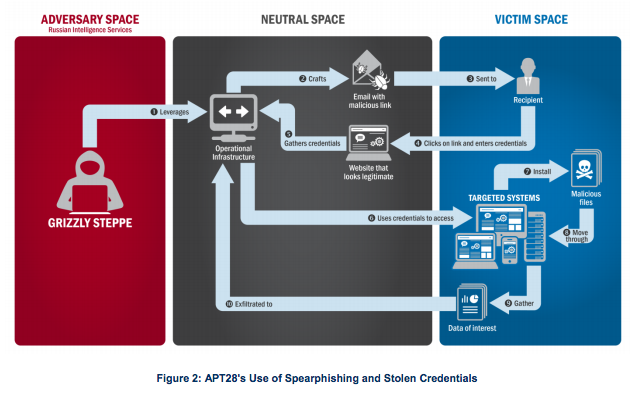
Here’s the illustration FBI and DHS officials, which they say shows how the Russian hacking group it calls APT28 stole the login credentials of US elected officials and others. Russian hackers continued to mount such campaigns, according to the report, with the latest one arriving in November 2016, just days after the US Presidential election.
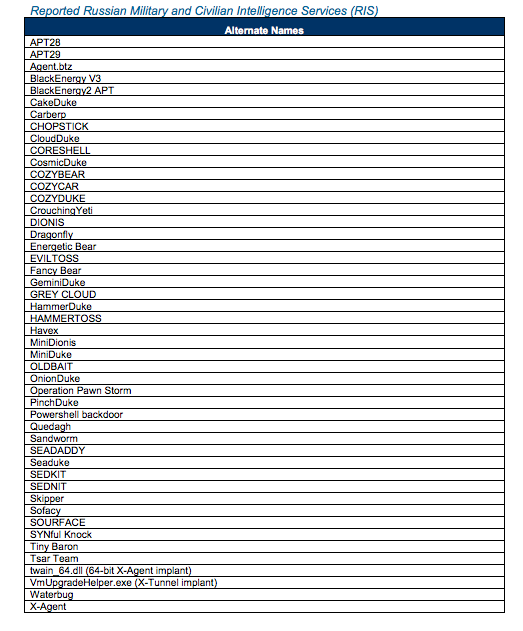
Here the names associated with Russian intelligence-backed hackers, according to the report. Some of the names — like CozyBear and FancyBear — are names this news site and others have written about over the last few years. A great discussion on CozyBear, in fact, can be found here, at CrowdStrike.
Earlier this month, Reid said he was certain the Trump campaign colluded with Russian hackers and Wikileaks in their efforts. To the Huffington Post, he said:
“Don’t put blindfolds on,” he said. “Here is the deal: We have a situation where during the campaign, especially the last few months of the campaign, WikiLeaks was heavily involved in trying to hurt Hillary Clinton and it helped Trump. And you have Trump who said he likes Putin better than he likes Obama.”
Here is the full text of the letter Sen. Reid sent to FBI Dir. Comey on October 30, 2016.
Harry Reid Letter to Director Comey 10-30-2016 by Gina Smith on Scribd
For aNewDomain, I’m Gina Smith.
Here is the JAR file of IP addresses FBI-DHS officials/security contractors say they found in their investigation of what they call Kremlin-ordered hacking of the American people.
Grizzly Steppe Report: JAR 16 IP Addresses, Russian Hacks of US Ev by Gina Smith on Scribd
Cover image of American troops in Vladivostok: by user Japanese-Marin via Wikimedia Commons.