aNewDomain — In The Republic, Socrates begins his account with a description of the occasion: “I went down, yesterday, to the Piraeus, with Glaukon the son of Ariston” to visit the Cave.
 The ancient allegory refers to the political realm of Socrates’ ancient Greece. But it’s also a good story about our present technological era.
The ancient allegory refers to the political realm of Socrates’ ancient Greece. But it’s also a good story about our present technological era.
We have a cave today. It’s called the DarkNet.
The Darknet
The DarkNet or Deep Web refers to the millions of secret websites hosted on networks like Tor or I2P, which are encrypted and inaccessible from regular Internet connection without using special software.
The WhiteNet, by comparison, is the Internet most of us are familiar with. It contains Google and other regularly indexed search engines.
Formerly the domain of lone hackers, the DarkNet has become the medium that operates approximately 90 percent of massive global Internet traffic.
The WhiteNet only accounts for 10 percent.
While people watch videos, share photos and email their mom on the WhiteNet, the DarkNet has become the driving force behind significant technological, marketing and cybersecurity breakthroughs.
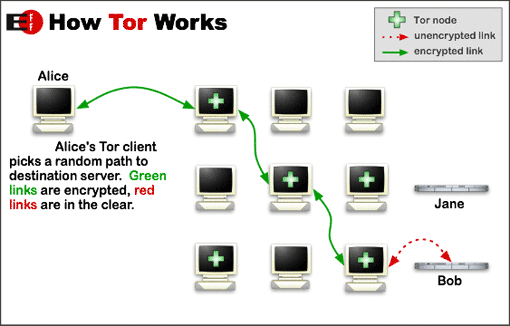 The DarkNet is accessed via Tor, an acronym for “the onion network.” Using “onion routing” to protect covert access to the Internet and anonymizing IP addresses to provide hidden encrypted services, the Tor Browser can be downloaded by anyone wanting to browse the DarkNet. Provided they know where to look.
The DarkNet is accessed via Tor, an acronym for “the onion network.” Using “onion routing” to protect covert access to the Internet and anonymizing IP addresses to provide hidden encrypted services, the Tor Browser can be downloaded by anyone wanting to browse the DarkNet. Provided they know where to look.
Tor was originally funded heavily by the U.S. government, and its security has been the subject of advanced academic research. They say that no serious known backdoors have been discovered in the system, which is widely used by media, government operatives and others wishing to conceal their true identity and location online. Activists and dissidents living under oppressive government regimes who fear detection and reprisal by government authorities for their Internet activities rely on Tor for keeping them safe.
Come To The Dark Side
Used heavily on the dark side of the platform, according to officials with giant global “think-tank” RAND Corporation, is cybercrime. The DarkNet allows the proliferation of a creeping landscape of nefarious electronic activity, RAND reports. Cybercrime black markets include:
- Withering attacks against individuals’ financial and transactional records, Twitter and other social media accounts.
- Targeting business and financial institutions, ranging from e-commerce and intellectual property to spying and seizing trade secrets.
- Conducting nefarious illicit and illegal services available for purchase, such as stolen credit card information.
- Child porn exploitation (perhaps the majority of DarkNet’s services).
- Terrorist propaganda, recruitment, planning, psychological warfare, mobilization, networking, sharing of information and fundraising.
- Purchase and sale of illegal goods, including arms purchases and stolen or otherwise illegal goods (although some DarkNet posts graciously disclaim the exchange of weapons of mass destruction).
- Drug ordering and delivery services which carry specific requirements for the most undetectable delivery to the customer’s doorstep. Drugs, for example, are promised to arrive in an innocuous envelope which is sealed airtight to avoid drug-detection dogs at airports and mail centers.
 Also noted in a recent RAND report:
Also noted in a recent RAND report:
“The black markets for cybercrime are both domestic and international in scope and the unique aspect of operating in cyberspace is that it is simultaneously nowhere specific yet everywhere.”
The players include lone hackers and sophisticated power brokers, including the Mafia, drug cartels, terrorist cells and even nation-states, particularly China, Latin America and Eastern Europe, which have the most quantifiable activities. However, Russia stills leads the pack as the “spy who loves (U.S.)” with the highest-quality DarkNet cybercrime.
Former FBI Director Robert S. Mueller, III published a widely cited report on The Threat of Homegrown Terrorism via cybercrime within U.S. borders:
Radical fundamentalists are particularly difficult to pinpoint in cyberspace. There are between 5,000 to 6,000 extremist websites on the Internet, encouraging extremists to initiate their own radicalization and to cultivate relationships with other like-minded persons.
Although we have destroyed many terrorist training camps in the past five years, extremists increasingly turn to the Internet for virtual instruction. Of course, not every extremist will become a terrorist. But the radicalization process has become more rapid, more widespread, and anonymous in this Internet age, making detection that much more difficult.”
 Shadows on The Wall
Shadows on The Wall
According to recent RAND reports — the “Hackers’ Bazaar” and “The Wild, Wild Web” — cyberspace has grown so large and complex that there is ever-increasing debate about how to handle it. Cryptography, the policies, trends, and means of assessing risks, vulnerability, and threat — they’re all undergoing constant change.
That’s according to Deepdotweb.com, an information clearinghouse on all matters DarkNet that’s run by anonymous volunteers. The site patterns itself after Google’s WhiteMarket search engine.
Encryption, the site explains,
Can take one of two forms — symmetric encryption which uses a shared secret that both parties must know in advance, or public key cryptography where the information to encrypt the information differs from the secret needed to decrypt the information.”
There’s more than one way to share whatever secrets you also want to keep.
Silk Road and the eBay of Illegal Goods
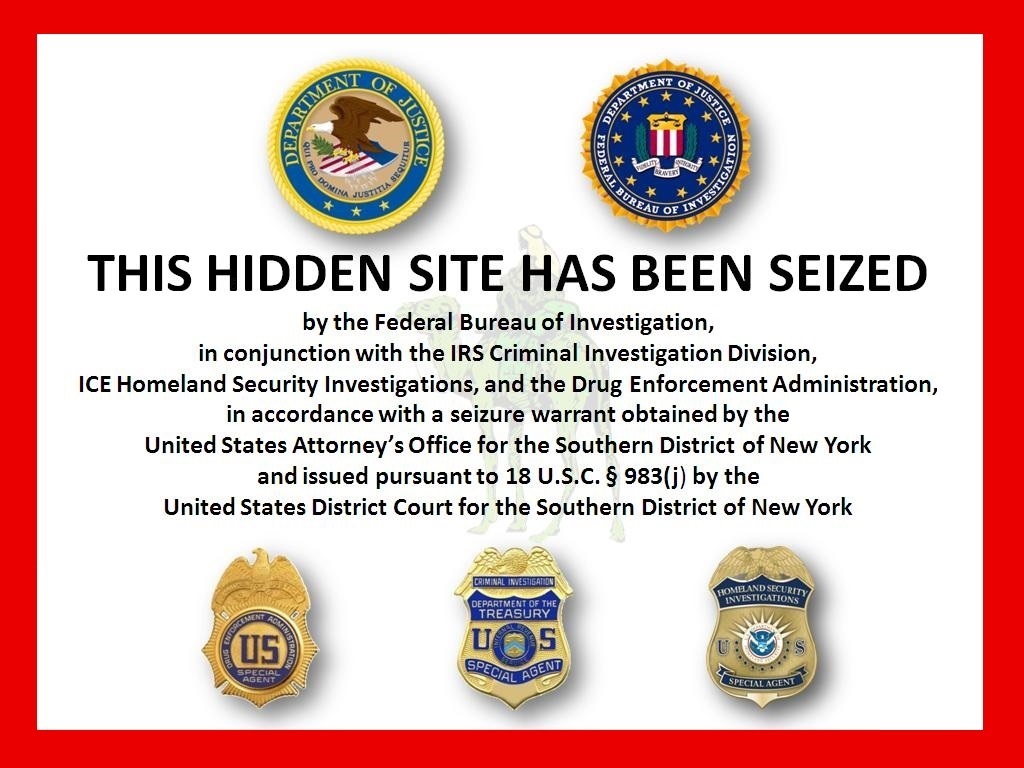
 The Darknet gained particular notoriety in 2013 as the “eBay of illegal goods” in the takedown of the Silk Road black market drug network.
The Darknet gained particular notoriety in 2013 as the “eBay of illegal goods” in the takedown of the Silk Road black market drug network.
Silk Road was launched in 2011 as a market for illegal drugs and, for a time, it was the undisputed leader in that market. The FBI shut down the website in 2013 and arrested and charged a 27-year-old Texas physics student with being the founder. The FBI alleges Ross William Ulbricht was the Dread Pirate Roberts, the man who made millions as secret leader of the DarkNet marketplace.
Silk Road succeeded for years due to a vast, highly compatible buyer/vendor base and effective controls to weed out scammers. So far nothing else has its trust level and popularity among users, although new contenders pop up all the time.
Silk Road 2.0, the successor and heir apparent to the first Silk Road, was seized in November 2014 during Operation Onymous. More arrests followed, including that of Blake Benthall, the alleged new administrator who operated under the handle Defcon. The government says Benthall linked parties and shared in the percentage of sale. The criminal complaint against Benthall alleges Silk Road was selling more than $8 million worth of drugs per month at the time of its seizure.
But the government says Silk Road was trading in more than narcotics.
 According to the FBI, the Dread Pirate Roberts offered to pay someone on Silk Road $80,000 to torture and execute a former Silk Road employee he thought had betrayed him. The hired killer was actually an undercover cop and this information was included in Ulbricht’s arrest affidavit.
According to the FBI, the Dread Pirate Roberts offered to pay someone on Silk Road $80,000 to torture and execute a former Silk Road employee he thought had betrayed him. The hired killer was actually an undercover cop and this information was included in Ulbricht’s arrest affidavit.
New sites constantly pop up to take another’s place. The Grams search engine has become popular after launching last year. Grams offers a way to search for products or “crawl” across the different DarkNet marketplaces. Its payment system is Bitcoin, the digital fluctuating currency on the DarkNet, and billed on Paypal by indexing broadening markets and using a scoring system similar to Google’s inventory standard that is “based upon how long the listing has been up, how many transactions, and how many good reviews,” according to a review on Reddit.
Industry: Google and Apple
 Tech industry leaders have championed encryption. Apple CEO Tim Cook, speaking this month at an awards dinner of the Electronic Privacy Information Center, described encryption as a cornerstone of privacy. He defended his decision to allow encryption of Apple’s communications portals, despite government efforts to have the private sector create backdoors into their products for their own uses.
Tech industry leaders have championed encryption. Apple CEO Tim Cook, speaking this month at an awards dinner of the Electronic Privacy Information Center, described encryption as a cornerstone of privacy. He defended his decision to allow encryption of Apple’s communications portals, despite government efforts to have the private sector create backdoors into their products for their own uses.
Cook said:
Some in Washington are hoping to undermine the ability of ordinary citizens to encrypt their data. We think this is incredibly dangerous. We’ve been offering encryption tools in our products for years, and we’re going to stay on that path. We think it’s a critical feature for our customers who want to keep their data secure. For years we’ve offered encryption services like iMessage and FaceTime because we believe the contents of your text messages and your video chats is none of our business.
Weakening encryption or taking it away harms good people that are using it for the right reasons. And ultimately, I believe it has a chilling effect on our First Amendment rights and undermines our founding principles.”
 A new generation of technology is bringing updated approaches to thwarting online attacks, including thickening firewalls and stricter access controls. Private firms have implemented “bug bounty” programs, with companies like Google rewarding those who report bugs and viruses. Bounties in Google’s “Vulnerability Reward Program” can run from $3,000 to $5,000, or up to $200,000 for identifying the most sophisticated bugs in large markets.
A new generation of technology is bringing updated approaches to thwarting online attacks, including thickening firewalls and stricter access controls. Private firms have implemented “bug bounty” programs, with companies like Google rewarding those who report bugs and viruses. Bounties in Google’s “Vulnerability Reward Program” can run from $3,000 to $5,000, or up to $200,000 for identifying the most sophisticated bugs in large markets.
But even Google hasn’t been totally “clean.” The company had to pay half a billion dollars to settle Department of Justice (DOJ) claims that it allowed ads for illegal online pharmacies that sold dangerous or addictive drugs. Now the National Association of Attorneys General says Google is at it again.
Hacking competitions are held to lure individual hackers to “go straight” and work for industry or the government. One popular competition is Pwn2Own, which paid out $850,000 last year.
Government Involvement and Fourth Amendment Issues
The government is maturing in how it identifies and monitors the DarkNet for cybercrime. Despite continued advances in encryption, says RAND cybercrime researcher and cryptologist Lillian Ablon, monitoring agencies are also growing in sophistication.

With cooperation between private companies and law enforcement, authorities are able to monitor encryption on point-of-sales activity and chips embedded in credit cards. Regular canvassing checks are conducted on black-market websites, among other strategies.
Edward Snowden, the former CIA employee and government contractor who in 2013 leaked classified information from the NSA, has both exposed and created complications in all of this.
As aNewDomain writer David Michaelis noted in “Vetting NSA and CIA Applicants and the Black Budget,” Snowden’s actions to expose the issue of state surveillance to the worldwide media continues to have ripple effects. As Michaelis said, “The process of vetting CIA and NSA applicants is turning out to be a real challenge — who exactly can you trust in the post-Snowden era?”
 Snowden himself remains a polarizing figure. Some hail him as a patriot hero who suffered personal risk to expose government wrongs. Others condemn him as a traitor spy who betrayed his country and should go to prison.
Snowden himself remains a polarizing figure. Some hail him as a patriot hero who suffered personal risk to expose government wrongs. Others condemn him as a traitor spy who betrayed his country and should go to prison.
For a time, according to Wikipedia, Snowden resided in Russia in an undisclosed location in temporary asylum. He has not yet faced the indictments against him for the Espionage Act by the DOJ.
However, the latest reports claim that Snowden currently resides in Hong Kong and is seeking extradition. The DOJ’s criminal complaint includes three active charges against him, which carry up to 30 years imprisonment, including fines and penalties should he return to the United States.
 Another government whistleblower, Thomas Drake, who also served with the NSA, challenged the DOJ and faced his charges under the Espionage Act. His concerns about wasteful government spending at the NSA and the government’s surveillance program involved the Trailblazer Project and the Thinthread Project. Like Snowden, Drake was charged for violations of the Espionage Act, which can carry the death penalty. The charges against Drake were later dropped, but he pled to a misdemeanor of misusing a computer.
Another government whistleblower, Thomas Drake, who also served with the NSA, challenged the DOJ and faced his charges under the Espionage Act. His concerns about wasteful government spending at the NSA and the government’s surveillance program involved the Trailblazer Project and the Thinthread Project. Like Snowden, Drake was charged for violations of the Espionage Act, which can carry the death penalty. The charges against Drake were later dropped, but he pled to a misdemeanor of misusing a computer.
A documentary, “Silenced,” was made about his case. According to reviews, Drake’s speeches provide a riveting account of Fourth Amendment considerations in his “privacy exercise,” which focus on the public’s right to know:
Put your life in a box, your documents, bank accounts, your passwords, everything — and give it to a total stranger — a fellow American for safekeeping. Would you do it?”
In his audiences, no one has ever said yes.
For aNewDomain, I’m Jim Kelly.
Images in order: The Allegory of The Cave via The British Museum; How Tor Works via Tor Project; by Ludovic F. Rembert for Privacy Canada.net; FBI Flag via Wikimedia Commons; Anonymous Woman by Beercha via Wikimedia Commons; Silk Road Seized via Wikimedia Commons; Inside a Mac Pro 2 via Wikimedia Commons; “Online Privacy and the Founding Fathers,” Adapted from “Declaration of Independence,” by J. Trumbull, 1819. Public Domain. Retrieved from Facebook User Page 2014″ by Facebook Inc. Copyright 2014 by Facebook Inc. Retrieved from Wikipedia, Adapted with permission from Wikimedia Commons; U.S. Navy Cyber Defense by U.S. Navy via Wikimedia Commons; Screenshot of Edward Snowden from “Citizenfour,” Laura Poitras / Praxis Films; Thomas Drake via Wikimedia Commons, All Rights Reserved













