aNewDomain – Last week, US-Cert released information on Grizzly Steppe, the malware used in the DNC hack.The IP and hash information in the US-Cert was lacking, though, so I decided to dig through it and see if I could make more of it.
Here’s what I started with …
Grizzly Steppe Report: JAR 16 IP Addresses, Russian Hacks of US Ev
I started out by running the IP addresses it gave through an ipinfo2sheets spreadsheet I put together earlier this year.
I was able to turn up a lot more detail …
Grizzly Steppe IP Analysis by J. Gamblin
Also, once I got more data for the IPs I noticed that it looked like there were a lot of TOR exit nodes on the list. So I cross referenced the IP addresses from the US-Cert against the TOR exit node list and 21% (191 of 876) of them were TOR exit nodes.
The fact that so many of the IPs are TOR addresses reveals the true sloppiness of the report.
Related: Grizzly Steppe: US Says Russia Hacked US to Influence Election [read report here]
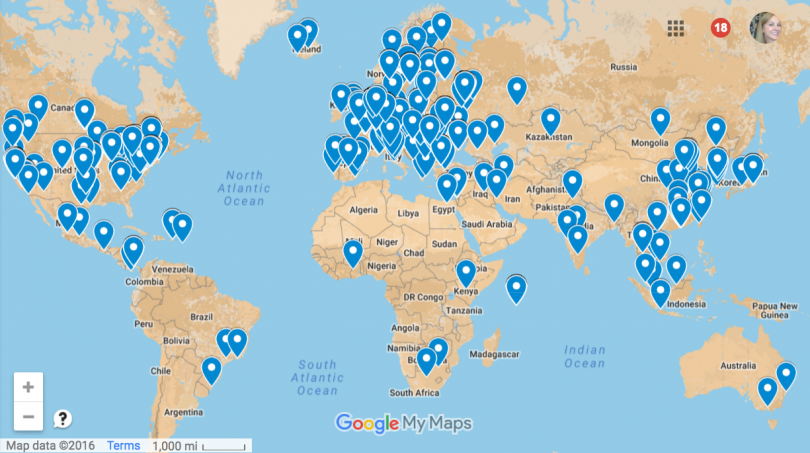
From there I decided to map the IPs on a Google Earth map to see where they were all located.
Next I looked at the hashes. According to VirusTotal, only 28 percent of AV detects the Grizzly Steppe files. I put a copy of this spreadsheet here.